

The first certificate flaw wasn’t some sort of malware or adware issue, says Dell representative Laura Pevehouse Thomas. Instead, it involved a security certificate used for customer support, called eDellRoot, “intended to provide the system service tag to Dell online support, allowing us to quickly identify the computer model, making it easier and faster to service our customers”, said Thomas. Luckily, Dell has already released a removal utility that will delete the compromising certificate (Computer World).
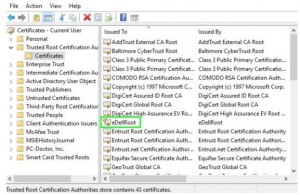

At first, Dell did not release a fix, nor acknowledge the DSDTestProvider issue, and it had many parties wondering why the company wouldn’t be as quick to provide help as it did to the first threat. It wouldn’t even respond to a request for comment, says Computer World. Luckily, the company did in fact release a downloadable tool for removing the root certificate. In the end, both the eDellRoot and DSDTestProvider certificates were threats of the same color. Because they both installed inside the Windows root store for certificates and used “private keys”, it allowed any hacker to play house with the certificates, get on malicious websites, and steal personal data. We can only hope that these current events can draw some sort of recognition to the fact that much more has to be learned about certificates in order to protect the systems they encompass. This is 2015, technology can’t always speak for itself.

 Laptop & Tablet Parts
Laptop & Tablet Parts




















